Online Threats: Network Attacks
Folks, this will be the last post of the "Online Threats" series and as people usually save the best thing for last, so do i (LOL!!!). The reason i think this online threat merits the last and best slot is because i think it is very creative and using it last is the best way to round up my discussions on online threats, even if the consequence of falling victim to the threat itself is annoying! I admit i had lots of fun studying this particular subject. Not that i would like to do the same by launching an attack on any websites, though.
To start things up, i would like to introduce you to a fictional scenario:
Here's the Story:
William's company, XYZ, decided to launch a brand new social website which allows members to discuss anything on blogs entries, critics' articles and global news related to computer science and technology. One of the website's features is related to the promotion of their own anti-hacking campaign which aims to reduce numbers of hacking-related incidents all over the globe. The feature received worldwide coverage, and was anticipated to be very effective against thwarting hackers all over the world. William slated the 20th of November 2008 as the official launch date of his company's social website. On the launch date, however, within a few minutes after the social website was launched, the server crashed, thus forcing the company to delay their web service for half the entire week.
(To be continued at the end of the article....)
Here's a first thought: what could be the reason for the occurence?
The reason is due to one online threat known as network attack; better defined as a Denial of Service Attack (DoS).
A DoS is a form of online attack which a person is capable of rendering a system unusable, or significantly slow it down by overloading its resources. An attacker who could not gain access to a machine are likely to apply a denial of service attack which crashes the machine. Hackers do this with the motive of preventing legitimate users access to a certain site and refraining them from using the service.
 Illustration on how a Denial of Service attack (DoS) functions
Illustration on how a Denial of Service attack (DoS) functions There are many ways a hacker can apply network attacks on a website; there are options such as flooding a network, disrupting connections between machines....but all methods reach the same intended consequences worldwide: networks are no longer operational, business organizations crippled and thus suffered financial loss, people's goodwill towards an organization fade out with every network attack directed at the organization.
Network attacks can be further classified from denial of service (DoS) into a more menacing form called a Distributed Denial of Service attack (DDoS), designed not just to bring a single website down, but the entire network down as well. To achieve that, hackers apply the use of botnets. Botnets are internet robots used for issuing a DDoS attack. As DDoS is a fairly large scale, coordinated network attack which inflicts the intended services through compromised systems, making the job of detecting it very difficult (as attacks can originate from several IP addresses).
Here's how an average hacker orchestrate a DDoS attack:
Step 1: Write a virus which will send ping packets to a target network/website.
Step 2: Infect a minimum of 30,000 computers with the virus and turns them into "zombie computers"
Step 3: Order the "zombies" to launch the attack by sending a "resurrection signal" to all of them.
Step 4: The zombies will start attacking the target server until every single "zombies" are disinfected.
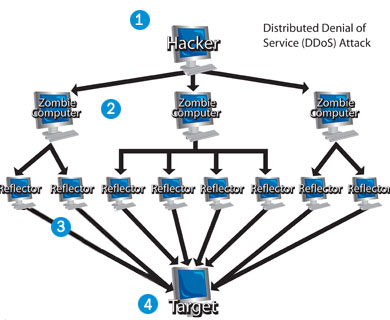
A zombie computer is an infected computer used to do a hacker's bidding, regardless of it being physically turned on or not. Zombie computer are capable of spreading themselves and infect other computers automatically.
It sounds like "Resident Evil", right? Luckily though, network attacks can be both detected and neutralized, just as how the zombies in Resident Evil can be killed with guns and swords...:)
Here's the sumarized list of what computer experts do to neutralize network attacks:
1. Detect and neutralize handlers (studying network traffic patterns and identify possible infections)
2. Detect & prevent secondary victims (reminding all users to update their PC security software & enforce tighter settings)
3. Detect & prevent potential attacks (packets filtering & firewall configurations)
4. Stop attacks (using methodologies such as Load Balancing, Throttling and Drop Requests)
5. Deflect attacks (A form of Counter-DoS by setting up honeypots to entice an attacker into revealing their actvities & strategies of launching network attacks)
6. Post-attack forensic (basically doing some homework after the launch of an attack such as traffic analysis)
Story A Continued.....
Hoping to solve the problem, William enlisted the aid of friend and professional white hacker, Jonathan to sort things out. Jonathan spent some time analyzing the network performance and was shocked to discover the evidence of huge Sync attacks directed at William's server. After making a detailed record, Jonathan revealed to William that his server had been hit with a DDoS by an enormous amount of spoofed internet protocols (IP). There are quite an amount of zombie computers connected on the internet, and they are all directed at William's server, which causes his server to crash due to a large amount of request for the server, rendering it unstable.
That's the end of the "Online Threats" series. I had shared a lot and i hope you will like it and will apply some of it in your daily computering life.
CHEERS!!!

0 opinion:
Post a Comment